How to Hide you IP Address | Change IP Address
After a lot of requests from various hackers across the world, we are coming up with this post on Hackytime. This post will tell you How to Hide Your IP Address or How to Change your IP Address
Read this if y0u want to know
What is Ip Address
Changing or Hiding the IP address is one of the biggest concerns of all Hackers as the IP Address can reveal the identity if the Hacker. Its just like your online address. If anyone can find your actual online address (IP Address), tracing you back won’t be that difficult.
Thus it is very important to hide or change your IP address before doing any kind of hacking attack or even think of doing so.
After getting hundreds of request on a tutorial on how to hide your IP address, here I am writing a detailed step by step tutorial on how to hide or change ip address.
We are using the proxy service called Hide my Ass (pro VPN).
What’s that? Let me explain in detail.
We all know about proxy servers. They help us to hide your ip address or
change ip address but there are many things you guys don’t know.
1) Free proxies are not completely anonymous – Your up can be disclosed by the website owner to the concerned authorities if needed.
2) Companies limit the maximum speed of browsing in free proxies – Say your internet speed is 8 Mbps, still using free proxies you can browse internet with a speed of only 265 kbps. This is irritating, isn’t it.
3) Many Webmasters can block users accessing free proxies.
There are different type of proxies. .
Even I wanted a reliable and Elite Proxy which can help me completely hide my Online Identity and what else could be better than changing my IP address every minute. I looked for many solutions online and then I found the PRO VPN of Hide My Ass.
To be very honest, in the beginning I was a bit confused when I saw the software. I was not very sure if it would work the way I wanted to but then I gave it a try. I thought of jiving it a try just for 1 month. It was just for $11.52 then , not it costs $9.99 only. I could actually think of spending $11.52 for my only if it gave me the kind on anonymity I wanted on internet. It helped me secure my online Identity online.
- Super fast, high speed elite / anonymous proxies. Elite proxies are 100 times more secure than free proxies
- I could select the country whose IP address I wanted in just 1 click. It offers over 38000+ unique IP Address from 53 different countries.
- I can set the timer to automatically change the IP Address. This way my IP Address gets changed every minute without me bothering to do so. If I am implementing a hacking attack, no-one could actually find my actual IP Address so I am always on the safer side.
- It anonymously encrypts all the traffic and works with all kind of platforms. Unlike free proxies the PRO VPN of Hide My Ass is not blocked by the websites. The traffic seems to be of legitimate human users, not proxies so on one can catch you using them.
I am giving away some screenshots for you guys so that you can have a look at what the software looks like.
Here is what the homescreen of the VPN looks like:
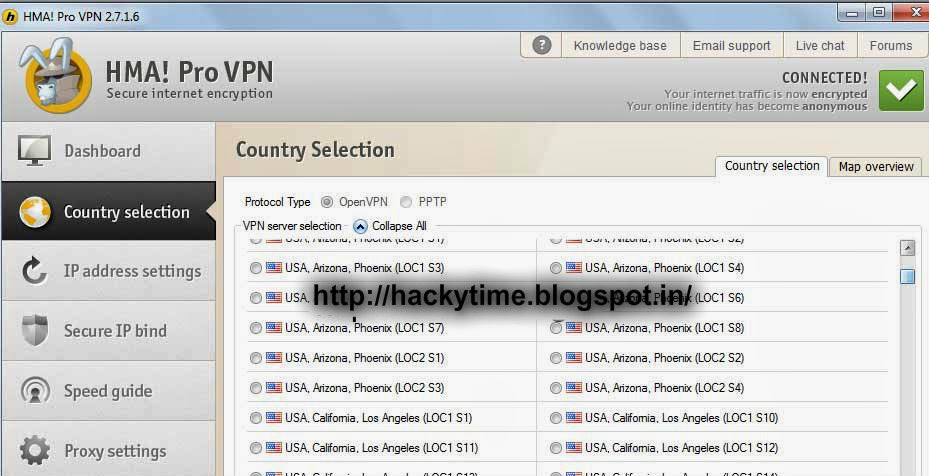
Once you enter the Software Dashboard, you get the interface shown.
We can select the IP Address of the country we want. There are 53+ countries and 38,000+ IP Address to chose from. Here is what the interface looks like.
We also get the provision to set the IP timeout ie we can select the time after which each IP Address should change and we get a new IP Address. It is a simple one click setting. Here is what the Set IP Timeout feature of Hide My Ass Pro VPN Looks like.vHiding / Changing your IP Address automatically was never so simple.
Finally last but not the least here I am showing how the changed IP Address
Now that you guys have everything infront you you, you can imaging how easy it is to change the IP Address automatically using the
Hide My Ass Pro VPN. This surely is the best proxy service out there. I was so overwhelmed by its response that I decided to write a detailed review about its performance.
If you are still in doubt just go and give it a try. It surely is worth it. I am sure you can spend $9.99 for your online security. It can actually have you from $$$$ loss and at the same time secure your online identity by making you anonymous.
There are many other benefits of using this service. This post has already become too long so will not stretch it more, maybe I will soon write another blog post for you guys describing how this Best Proxy Service can help you from getting hacked and increase your online security by continuously changing your IP Address.
Give it a try and share your views. Waiting for your feedback!






![[Image: PwnSTARscreenshot.png]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh7hxjJWz3ZeScwsEMbDXOsIp6KpUviswNNmxoB06NOYfSlYwwnPw_9DRmHjWN7Q0UPGmptofvXyb7M1SVH7hyphenhyphenwVODrf6mWxV4-pfG-ldP-ovWg6d5PfzUvuiMjw1M_QgIDj7f8ONPrSqm8/s640/PwnSTARscreenshot.png)
![[Image: zap1-3historyfilter.jpg]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhIiygNYf1__WzGkjqlYGgf3thtOXl1pZwZOOAfiQND7FzdNwVl_wCnVYCUhDo6A1cAydSgyO7-5IHHV4lOESjElV7BmyySaqA7QNvwrJWxqooiLKFJaAqvk7rgGg2yzXguoeSUTC7JSpug/s640/zap1-3historyfilter.jpg)
![[Image: Set-Box_2.png]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjayf59aZcWzvYQQgfRklH3ja6FESaB8YTYGXdZ0DwQdMPtoTFS8zKobHUr4wEBr6qt-itcZj-sF7dTJ6qPTrOf4ahQXDp1y9MddIFK5a_kkSaLCldGVdU7wJS3Afby-NfEh59C1WS3vEoW/s320/Set-Box_2.png)
![[Image: scanner.png]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiGDfeM590X8B7pkWdMLlldP9mOpVYi-zmmINiHYv9edjj6pZRtvyOxNAVvFHWfbm1ZrLZ1YVoVqEsyvMZNfKfDP6zBhF9uUjkpZb3NUoQf8CuntRS21xWXASewCGBOryu5pUjozFarGiMe/s640/scanner.png)
![[Image: Ettercap_2.jpg]](http://i1-linux.softpedia-static.com/screenshots/Ettercap_2.jpg)
![[Image: SANS+Investigative+Forensic+Toolkit+2.14+Released.jpg]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjl4LrLY9tr6XohWVnDS6udkcdYIpXp3PTOStpI6z1NPVZA3CgYiE77IhDkTXEBGfgDtSWfdg-iGw7aI6Os56TI82LKUrGmVHz7ZssiTX2i5wCw2fKCRqS9VAH3FKOs4mUyS56gI0aoLgOQ/s1600/SANS+Investigative+Forensic+Toolkit+2.14+Released.jpg)
![[Image: ws-main.png]](http://www.wireshark.org/docs/wsug_html_chunked/wsug_graphics/ws-main.png)
![[Image: WebSploit+Framework+2.0.3+with+Wifi+Jammer.jpg]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEitZl4cAf0MV5X-Gf89dff4OwtIMNZjSKYOk7XBO8UCOQoM7uiA4xwfPF5wsyCTWPW3DomnbbHM6uwqZV7mfyTZHRx9o4s81PB2rl8tkdU1dpR-xFl1OQMZeZTooS1E5dOUQOUP5sn04PZH/s640/WebSploit+Framework+2.0.3+with+Wifi+Jammer.jpg)
![[Image: winAUTOPWN+v3.2+Released.jpg]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjOAhWZnP7khoxcaqyRZWN27g016TLL5GicNyvNoVLF5M0sx1yzPSQ2oZ1YyNQi5AaDh__c_YJjKrbOgEuSyHKQzmEUdmrh5xEX1ESPF5NQ2tLOAXGPDPqIsSsevHLD19FVkuFQLr6SAP8K/s640/winAUTOPWN+v3.2+Released.jpg)
![[Image: hashcat.png]](http://hashcat.net/hashcat/hashcat.png)














